|
Information
about user interactions with Cyberenvironment components is captured and used
to provide project documentation and to support coordination, alerts,
subscriptions, and knowledge network recommendations.
|
||
|
|
|
|
|
|
|
|
|
|
Funding for ECID technology development comes from the
National Science Foundation and the Office of Naval Research. Interested in ECID?
Join the ecid-support list by sending email to majordomo@ncsa.uiuc.edu with the phrase "subscribe ecid-support" in the body of the email. |
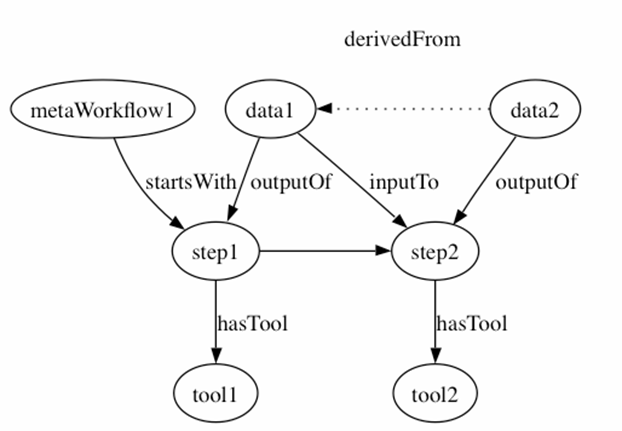
Cyberenvironment
components log descriptions of user interactions, which are captured as
metadata represented using the Resource Description Framework (RDF) via
NCSA’s Tupelo 2
Toolkit. RDF metadata and URI-based globally unique identifiers allow the
cyberenvironment to merge information from multiple components and build
provenance networks describing complex user activities. For
example, a provenance network might show relationships between two data
objects and a meta-workflow. Associating data objects with their roles as
input and output to steps in the provenance graph makes it possible to infer
the derivation of "data2" from "data1." By adding nodes
and arcs to this kind of graph, we link user interactions in discussion
forums with tool use patterns in workflows (see CyberIntegrator),
to provide targeted recommendations (see CI-KNOW) and other contextual user
support. |
|
|
|
|
|
|
|
|
|
|
|
|